Monthly Cyber Digest

Cyber Vigilance: What You Need to Know
This month’s cyber digest focuses on cyber vigilance—the proactive mindset needed to stay ahead of evolving threats. With ransomware, phishing, and zero-day exploits on the rise, businesses must combine technology with awareness to protect their data and reputation.
Network Visibility & Ransomware Risks
- Enable Multi-Factor Authentication (MFA) for all users.
- Run phishing simulation training quarterly to test and educate staff.
- Review your Microsoft Secure Score monthly to identify and fix gaps.
- Use Microsoft Intune to manage mobile devices and enforce app policies.
- Keep systems patched and monitor for unusual activity.
Cyber vigilance is not a one-time fix—it’s a continuous process of improvement and awareness.
October Cyber Security News
Network Visibility & Ransomware Risks
Most teams lack visibility into east-west network traffic and hidden ransomware risks. Illumio Insights now offers instant mapping of cloud and on-prem traffic, automatic detection of ransomware exposure, and one-click attack containment. Early testers have uncovered legacy vulnerabilities and risky open protocols within hours. Try Illumio Insights free for 14 days to see your real exposure and strengthen breach containment.
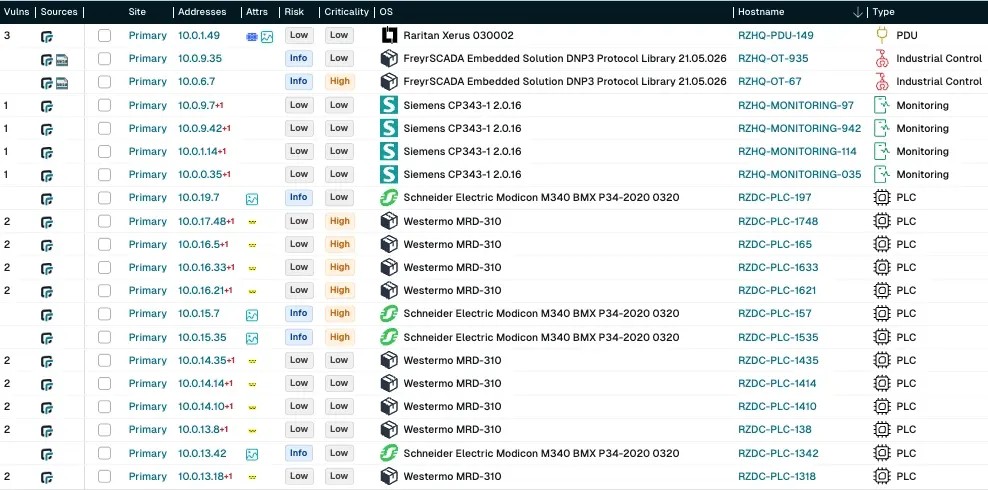
OT Asset Inventory: CISA Guidance
The latest CISA guidance emphasises the importance of knowing every asset in your network. runZero breaks down five steps to building a comprehensive OT asset inventory and explains how visibility across IT, OT, and IoT is now essential for critical infrastructure. Move from inventory to action with risk management, maintenance, and monitoring.
AI-Powered Defence: Synack & Tenable Partnership

Attackers are leveraging AI for faster strikes. The new Synack + Tenable partnership blends AI-assisted triage with human-led pentesting, turning vulnerability insights into actionable defences. This approach helps organisations translate assessment results into real-world protection.
AI-Driven Supply Chain Breach: s1ngularity
Malicious Nx packages published to npm compromised thousands of GitHub repos, using AI tools to steal credentials and modify files. Developers using Nx, GitHub Actions, or AI tools in build pipelines should review the full breakdown and remediation checklist from OX Security.
Zero-Click Exploit Targets Microsoft 365 Copilot

The EchoLink vulnerability (CVE202532711) allows attackers to compromise Microsoft 365 Copilot security via hidden prompts in emails and files. Enforce least privilege, monitor critical settings, automate policy enforcement, and consider third-party tools like CoreView for enhanced protection.
Endpoint Security Effectiveness

Horizon3.ai’s NodeZero safely validates endpoint defences in production, mapping adversarial behaviours to MITRE ATT&CK. It provides proof of protection, identifies unprotected hosts, and ties endpoint coverage directly to business risk.
Identity Security: Maturity vs. Reality

While 70% of organisations believe their identity security is mature, 80% lack complete visibility into threats. Osterman Research highlights the need for continuous visibility, risk scoring, and autonomous response as the new gold standard for identity security.
UK Public Sector: Supply Chain Resilience
State-sponsored threat actors are targeting the UK public sector. The Government Cyber Security Strategy (GCSS) aims for resilient supply chains by 2030. Risk Ledger’s guide explains how to gain visibility into third-party risks, collaborate with peers, and align with CAF principles.
CrushFTP Vulnerability: CVE-2025-54309
A critical authentication bypass vulnerability affects CrushFTP. Update to the latest version or enable DMZ proxy as a mitigation. Vicarius Labs offers a non-invasive workaround to reduce exposure.

Top Cyber Security News Picks

- Threat Actors Abuse X’s Grok AI: Hackers use Grok to bypass link posting restrictions and spread malicious links on X.
- Disney Settles $10M Over Kids’ Data on YouTube: Disney pays $10 million for collecting children’s data without consent, highlighting the importance of COPPA compliance.
- Sitecore Zero-Day Exploited: Attackers exploit a legacy vulnerability to deploy malware via ViewState deserialization.
- Palo Alto Networks Data Breach: OAuth token theft exposes customer data and support cases in a supply-chain attack.
- Google Fined $379 Million: French regulator fines Google and Shein for cookie consent violations, underscoring the need for transparent data practices.
Reflective IT Tip
Stay vigilant: review your network visibility, update vulnerable systems, and ensure identity and endpoint security are continuously monitored. Regularly check regulatory updates and supply chain risks.
Need Help Navigating Cyber Threats?

Reflective IT offers expert guidance on network security, compliance, and incident response. Contact us today to strengthen your cyber resilience.
📞 0207 317 4535 | 📧 support@reflectiveit.com
