Cyber Insurance in 2026 – What to Prioritise

Cyber Insurance in 2026: Why Requirements Are Getting Tougher
Cyber insurance has rapidly evolved over the past two years, and 2026 marks the strictest underwriting standards yet. Insurers have shifted from reactive coverage to a risk‑selective model—approving only organisations that can demonstrate strong, continuous security controls.
With ransomware sophistication increasing, business email compromise at record highs, and supply‑chain attacks escalating, insurers now require far more than basic cybersecurity hygiene. If you’re renewing or applying for cyber insurance this year, preparation is essential.
Top Priorities for Cyber Insurance Approval in 2026
Across industry guidance, insurer requirements, and analyst insights, several control categories consistently appear:
- Multi-Factor Authentication Everywhere: MFA must be deployed across all cloud apps, VPNs, privileged accounts, and remote access solutions. Partial deployment will now trigger automatic rejection.
- Email Threat Protection: Insurers now expect advanced anti‑phishing technology—not just basic spam filtering. AI‑driven inbox defence is becoming a minimum requirement.
- Endpoint Detection & Response (EDR): Traditional antivirus alone is no longer accepted. Continuous behavioural monitoring and automated containment are mandatory.
- Privileged Access Management: Insurers require enforced least‑privilege, secure admin accounts, and regular access reviews.
- Backup Hardening: Immutability, offline copies, and regular recovery testing are essential to qualify under ransomware‑related policies.
- Security Awareness Training: Annual training is no longer enough—insurers want evidence of continuous phishing simulations and behavioural improvement.
- Incident Response Planning: Organisations must demonstrate a tested incident response plan with named roles, severity triggers, and forensic readiness.
The Rise of Continuous SecOps Expectations
In the past, insurers assessed cybersecurity posture based on a static questionnaire. In 2026, insurers increasingly expect continuous security operations. This shift is driven by the fact that cyber risk changes too quickly for annual reviews to provide accurate underwriting assessments.
Continuous SecOps includes:
- 24/7 monitoring of endpoints, identity, and network activity
- Automated alerting and threat correlation
- Regular patching with strict timelines for critical vulnerabilities
- Ongoing configuration reviews against a baseline standard
- Real‑time detection of account misuse or credential theft
Organisations lacking these controls may face higher premiums, reduced coverage, or outright denial.
Minimum Controls Checklist for 2026
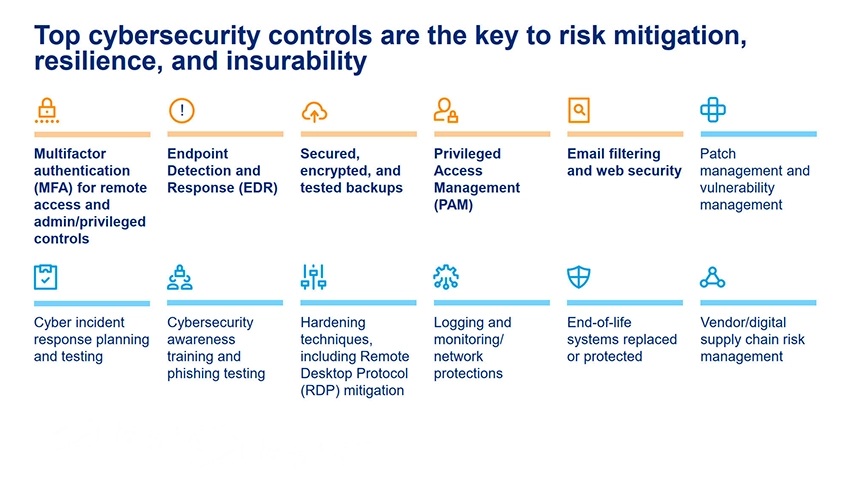
According to cybersecurity experts, SMBs and mid‑market organisations need the following minimum controls to be considered insurable:
- Modern Authentication: MFA + conditional access across all systems
- EDR/XDR Deployment: Replacing legacy antivirus
- Email Security + DMARC: Anti‑phishing, anti‑spoofing, impersonation protection
- Secure Backups: Immutable, encrypted, regularly tested
- Privileged Identity Management: Admin isolation, JIT access, password rotation
- Vendor/Supply‑Chain Risk Management: Documented third‑party controls and evidence of annual review
- Firewall + Zero Trust Controls: Network segmentation and identity‑driven access
- Documented Security Policies: Incident response, acceptable use, BYOD, change control
Insurers now require evidence, not declarations, of these controls. Screenshots, audit logs, and reports may be requested during underwriting.
How Phishing and Social Engineering Impact Premiums
Phishing and social engineering remain the biggest sources of cyber insurance claims. Because of this, insurers are emphasising:
- Mailbox‑level threat detection powered by AI
- User‑reported phish analysis workflows
- Automated inbox remediation
- Behavioural analytics to detect anomalous identity usage
Companies deploying advanced anti‑phishing platforms are seeing significantly reduced premiums compared to those relying on legacy email filtering alone.
What Underwriters Want to See in 2026
Cyber insurers now focus on risk reduction, not just historical data. Underwriters typically request proof of:
- Zero Trust identity enforcement
- Full visibility into devices, apps, and user behaviour
- Rapid detection and automated response capabilities
- Vendor access restrictions and monitoring
- Documented forensics capabilities
- Evidence of regular disaster recovery tests
- Patch SLAs for critical vulnerabilities (often < 15 days)
Meeting these requirements can dramatically improve approval odds and reduce premium costs.
How Reflective IT Can Help You Meet 2026 Requirements
Navigating cyber insurance is increasingly complex—but we help simplify it. Reflective IT supports organisations by:
- Conducting pre‑underwriting security assessments
- Strengthening controls required by insurers (MFA, EDR, Zero Trust, backups)
- Deploying advanced phishing defence tools
- Implementing continuous SecOps monitoring
- Providing documentation required during renewal
Our goal is to help your organisation qualify for coverage, reduce premium costs, and ensure a strong cybersecurity foundation.
Reflective IT Tip
Start preparing for cyber insurance renewal at least 90 days in advance. Many controls require time to implement—and underwriters increasingly expect evidence, not promises.
Prepare for Your Renewal with Confidence

Contact Reflective IT today to assess your readiness for cyber insurance and strengthen your cybersecurity posture.
📞 0207 317 4535 | 📧 support@reflectiveit.com